SQL Injections, by R. Patterson
SQL Injections
Rayvorn Patterson
Towson University
Computer Science Security Track
rayvorn@gmail.com
Abstract
Structured Query Language Injections (SQL injections) have emerged as a serious threat to many web applications and is in the top ten vulnerabilities for web applications (WhiteHat, 2011). In this paper we explore the basics of SQL injections as well as a real world exploit example.
General Terms
Documentation, Experimentation, and Security
1. Setup
The following tools and software were used in this experiment:
1.PHP Version 5.3.3
2.MySQL Server Version 5.1.66
3.CentOS release 6.2 (Final)
2. Introduction
This paper details SQL injection vulnerabilities in web applications. We wish to explain a simplistic approach to SQL injections and a real world example.
To fully understand SQL injections it is necessary to understand the basics of SQL and PHP.
2.1. Introduction to SQL
SQL is a programming language designed to interact with and manage data. SQL is used for three main reasons: creating a database and defining its structure, querying the database to retrieve data, and controlling database security. This paper focuses on SQL injections and will focus on SQL queries in this section (Wilton & Colby, 2005).
A SQL Query poses a question to the database which answers with the matching data. “A SQL query consists of various statements, clauses, and conditions. A statement is an instruction or a command. For example, “Get me some data” is a statement. A clause specifies limits to a statement, the limits being specified using conditions.” (Wilton & Colby, 2005) For example if we wish to select all users for a MySQL database the query looks like:
SELECT user FROM mysql.user To select only the user with the name root the query would be: SELECT user FROM mysql.user WHERE user=”root”
SQL injection is injection a query into a web application. Queries are used in SQL injection attacks to directly interact with the database backend of a web application. “[SQL injections] exploit the web application; as a result the attacker may gain unauthorized access to a database or to retrieve information directly from the database.” (Patel, Mohammed, & Soni, 2011)
2.2. Introduction to PHP
The official name for PHP is “PHP: Hypertext Preprocessor and it is a server-side scripting language.” (Meloni, 2004) PHP is used to write dynamically generated web pages and can access databases. Its access to databases could allow SQL injections if the input is not properly sanitized.
3. Login SQL vulnerability
A simplistic example is derived from the code at PHP Sense. The changes in the code include the deletion of all input validation the files login-exec.php and register-exec.php. For this particular example we shall only look at login-exec.php.
3.1. Examining the Code
With the deletion of the input sanitization clean function we now have a vulnerable input for variables $login and $password as shown here (around lines 25-26 after deleting clean function):
$login = $_Post[‘login’]; $password=$_Post[‘password’];
If we wish to properly see the queries we are injecting we need only to add a few lines of code for when the query fails as shown here (These lines of code are around line 64):

The above code causes everything to cancel and directly output the query to the screen if the query or login fails.
3.2. Exploitation
Visit the local website that is hosting the login application. Now we shall attempt to use an SQL injection on the password field. To do this we first enter anything into the username field to avoid the input being empty. Then we try a simple SQL injection of ‘1=1. Our result is something like this:


Notice that the output given has a “randomized” output for the password field. This is due to the hashing function for the password field used in the code around line 47:
![]()
Now if we try using the same exploit on the login field we get the following result:


Notice that our injection was successful however our query syntax is wrong because of an extra single quotation mark. It should also be noted that 1=1 statement is AND together with the password thus it will most likely fail. To fix this we use the below SQL injection:
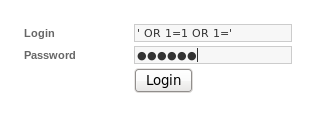
We then obtain a successful login screen:

This is a very simple SQL injection example that may not seem very practical. To explore a more practical SQL injection vulnerability we look for real world examples in the following section.
4. Wordpress All Video Gallery 1.1 SQL Injection Vulnerability
To look for a real world example of SQL injections we visit Exploit Database and go to the web applications section. The vulnerability for WordPress All Video Gallery is suitable because it comes with exploitation code and the vulnerable application. In this paper we will forgo how to install the actual WordPress application and instead give instructions on installing the WordPress plugin. Instructions on how to install WordPress can be found here.
4.1. Installation
To install the WordPress plugin we first unzip the application zip file from Exploit Database on our local web host server. We do this by using the command:
![]()
Note that the first directory is the location of your zip file and the second directory is the location of your plugins folder on the WordPress server. Now we login as an administrator on your WordPress server and click plugin on the menu on the left. Then activate the All Video Gallery plugin as shown below:

Now to add a video to the galleries click the All Video Gallery button at the bottom of the menu on the left. Click the category tab at the top and add a new category. Similarly do the same for the videos tab when adding a video.
We now need to modify the /var/www/html/wp-content/plugins/all-video-gallery/config.php so that we can properly see the output of our injected queries (this is for demonstration purposes). We do this by adding a simple echo of the two variables around lines 39 and 40 as shown below:

4.2. Exploitation
Before we enter the exploit code we verify our application is working by visiting the page with our browser to see what it returns if we try to select an appropriate video:
http://localhost/wp-content/plugins/all-video-gallery/config.php?vid=1&pid=1
As expected the variables should both be displayed on the webpage as 1. Now we try injecting the given code from Exploit Database onto our webserver through the browser:
http://localhost/wp-content/plugins/all-video-gallery/config.php?vid=1&pid=11&pid=-1+union+select+1,2,3,4,group_concat(user_login,0x3a,user_pass),6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41+from+wp_users--
Perhaps unexpectedly the variables are just 1 and -1. If we look at the config.php file again you should notice that both variables are being cast as integers. This variable casting prevents the SQL injection we are trying to execute. For experimental purposes we remove the integer casting from the $_pid variable. We should now have an output of:

Notice the query is successfully injected and that we obtain an output of the WordPress users.
Bibliography
Meloni, J. (2004). PHP 5 Fast and Easy Web® Development. Boston, MA: Thomson.
Patel, N., Mohammed, F., & Soni, S. (2011). SQL Injection Attacks: Techniques and Protection. International Journal on Computer Science & Engineering, 1.
WhiteHat. (2011). WhiteHat Website Security Statistic Report. Retrieved December 05, 2012, from WhiteHat Security: https://www.whitehatsec.com/assets/WPstats_winter11_11th.pdf?doc=WPstats_fall10_10th
Wilton, P., & Colby, J. W. (2005). Beginning SQL. Hoboken, NJ: Wiley.